Integrate WorkOS with MCP Servers
This guide explains how to add WorkOS authentication to MCP servers using an API-first approach. You will deploy authentication directly from an OpenAPI (Swagger) specification without writing backend code.
Introduction
WorkOS provides enterprise authentication for applications. MCP servers require authentication to secure MCP Tools and user access. This guide shows how to connect WorkOS authentication to MCP servers using OpenAPI specifications and the HAPI server.
Prerequisites
Before you begin, ensure you have the following:
- A WorkOS account with an organization.
- A WorkOS application with Dynamic Client Registration (DCR) enabled.
- The HAPI server CLI installed.
- An OpenAPI (Swagger) specification v3 for your API.
- MCP Inspector or any MCP client application supporting authorization flow.
Configure WorkOS
You must configure WorkOS to enable authentication for your MCP server.
- Create an organization and add users in WorkOS.
- Create a WorkOS application and enable Dynamic Client Registration (DCR).
- Set up redirect URIs to the Application (MCP Inspector or your MCP client).
Dynamic Client Registration allows MCP servers to register applications in WorkOS automatically if no client ID is provided.
Define API Security in OpenAPI Specification
Extend your OpenAPI specification to include authentication and CORS settings.
- Add a security definition for OAuth2, specifying the client ID, authorization URL, and token URL.
- Configure CORS to allow requests from the MCP Client.
WorkOS provides a .well-known authorization endpoint.
If your API does not provide a .well-known authorization endpoint, HAPI server generates one automatically.
Start the MCP Server
Start the MCP server using your OpenAPI specification.
hapi serve demo -f "api.yaml" --headless
# or
hapi serve https://docs.mcp.com.ai/apis/openapi/demo.yaml -f "api.yaml" --headless
Example files:
This command loads your API spec with security and runs the MCP server in headless mode for backend integration.
Connect MCP Server to WorkOS
You can authorize Apps (MCP Clients) with WorkOS (Authorization Server) in two ways:
Authenticate with Client ID
- Provide the WorkOS client ID in your configuration.
- Users log in through WorkOS (for example, only users from
@example.com). - MCP application Client is approved.
Authenticate with Dynamic Registration
- Remove the client ID from your configuration.
- Start the authentication process.
- WorkOS automatically registers a new application for your MCP.
WorkOS creates a new application entry (such as "MCP Inspector") without manual dashboard changes.
Review Authentication in WorkOS
After authentication, verify the following events in the WorkOS dashboard:
- Users are authenticated successfully.
- Applications is dynamically created, if using DCR.
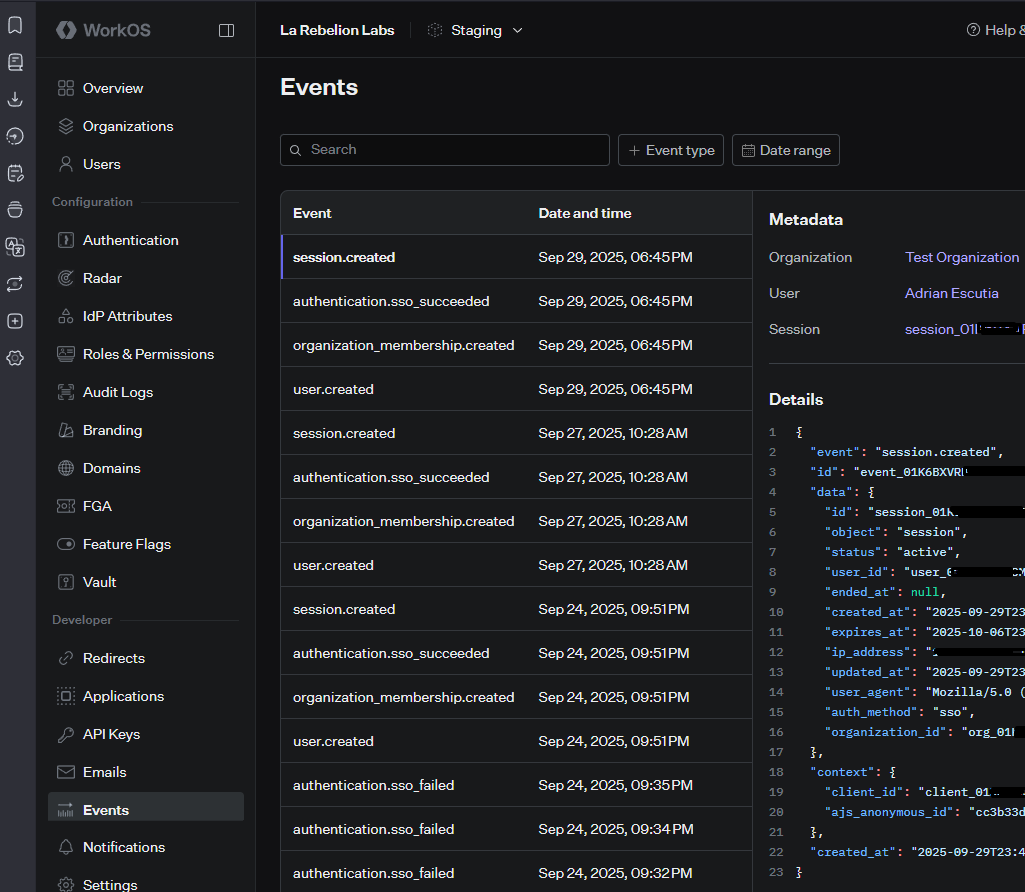
Demo Authentication with WorkOS
Wrapping Up
You have integrated WorkOS authentication with MCP servers using OpenAPI specifications and the HAPI server. This approach enables secure, API-driven deployments without backend code.
You can now deploy MCP servers with authentication quickly and efficiently.
With the HAPI Server, you can:
- Deploy MCP servers straight from OpenAPI specifications (OAS).
- Add authentication via WorkOS.
- Do it all without writing a single line of backend code.
This makes it incredibly fast to go from API spec → secure MCP server.
To request integration with another API or authentication provider, contact the team.
Be-HAPI and go rebels! ✊🏽